The newly developed tool by hackers, the InstaHax0r Works on the bases of Rainbow Tables to hack the Instagram Passwords of users. As we all know that the passwords on a computer are not saved or stored as plain text. But are molded into a secure encryption model using special codes.
So the new famous InstaHaxor tool is using the same Rainbow Tables technique to unearth many mysterious passwords sets by users. But it’s still the basic method of hacking an Instagram account. It affects mostly the accounts that are badly secured.
How Rainbow Tables Work:
Here is just a small example to let you know how the Rainbow tables work in extracting the most secure details.
A rainbow table works by doing a cryptanalysis very quickly and effectively. Unlike bruteforce attack, which works by calculating the hash function of every string present with them, calcuating their hash value and then compare it with the one in the computer, at every step. A rainbow table attack eliminates this need by already computing hashes of the large set of available strings. There are two main steps in this:
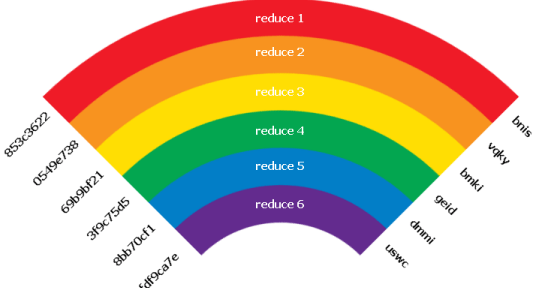
Creating a Table
Here, the hash of a string is taken and then reduced to create a new string, which is reduced again, repeatedly. For example, let’s create a table of the most common password, 12345678, using MD5 hash function on first 8 characters:
- First we take the string and pass it through md5 hash function.
hashMD5(12345678) = 25d55ad283aa400af464c76d713c07ad- We reduce the hash by taking only the first 8 characters. Then, we re-hash it.
hashMD5(25d55ad2) = 5c41c6b3958e798662d8853ece970f70- This is repeated until enough hashes in output chain. This represents one chain, which starts from the first plain text and ends at the last hash.
- After obtaining enough chains, we store them in a table.
How to survive Tools like InstaHax0r:
Since we all know that InstaHax0r App uses the new Rainbow tables procedure to crack into anyone’s passwords. So we need to survive such attacks.
The best way to get rid of such tools is to set 2-way authentication on all your accounts. InstaHax0r may be just a single tool. There are hundreds of them out there. But if you choose the dual-authentication process you can easily survive 99% of the attacks.
Is a freelance tech writer based in the East Continent, is quite fascinated by modern-day gadgets, smartphones, and all the hype and buzz about modern technology on the Internet. Besides this a part-time photographer and love to travel and explore. Follow me on. Twitter, Facebook Or Simply Contact Here. Or Email: [email protected]


![Top 5 Best iPhone Hacking Apps [2019] Best iPhone Hacking Apps](https://axeetech.com/wp-content/uploads/2019/08/Top-5-Best-iPhone-Hacking-Apps.jpg)

